In May 2021, drivers in Florida, Georgia and other neighboring states encountered a strange sight along the road: all but a few gas stations were closed down, out of fuel. This chaos wasn’t caused by a natural disaster, nor the pandemic, but a single compromised password. The Colonial Pipeline, one of the biggest fuel suppliers for the East Coast, had fallen victim to a cyber attack. The breach, which led to a $5 million ransom payment, targeted the most vulnerable component of security systems worldwide: people.
“95% of security breaches are caused primarily by human error rather than technical vulnerabilities,” points out Cosmin Mihai Tarsichi, Python Tech Lead. In 2023 alone, there were 343 million cybersecurity victims worldwide and a 72% increase in breaches since 2021. “We’re seeing an average of 450,000 new malicious programs created daily,” Cosmin says. “But what’s truly concerning is that 98% of successful cyberattacks rely on social engineering rather than pure technical exploitation.”

“Understanding how is just as important as understanding why”, adds Peter Hudak, Offensive Security Team lead at ABN AMRO Clearing. Peter’s job is to get inside the minds of technological criminals and try and emulate their thinking and their actions in order to better protect sensitive data in companies.
The human security gap
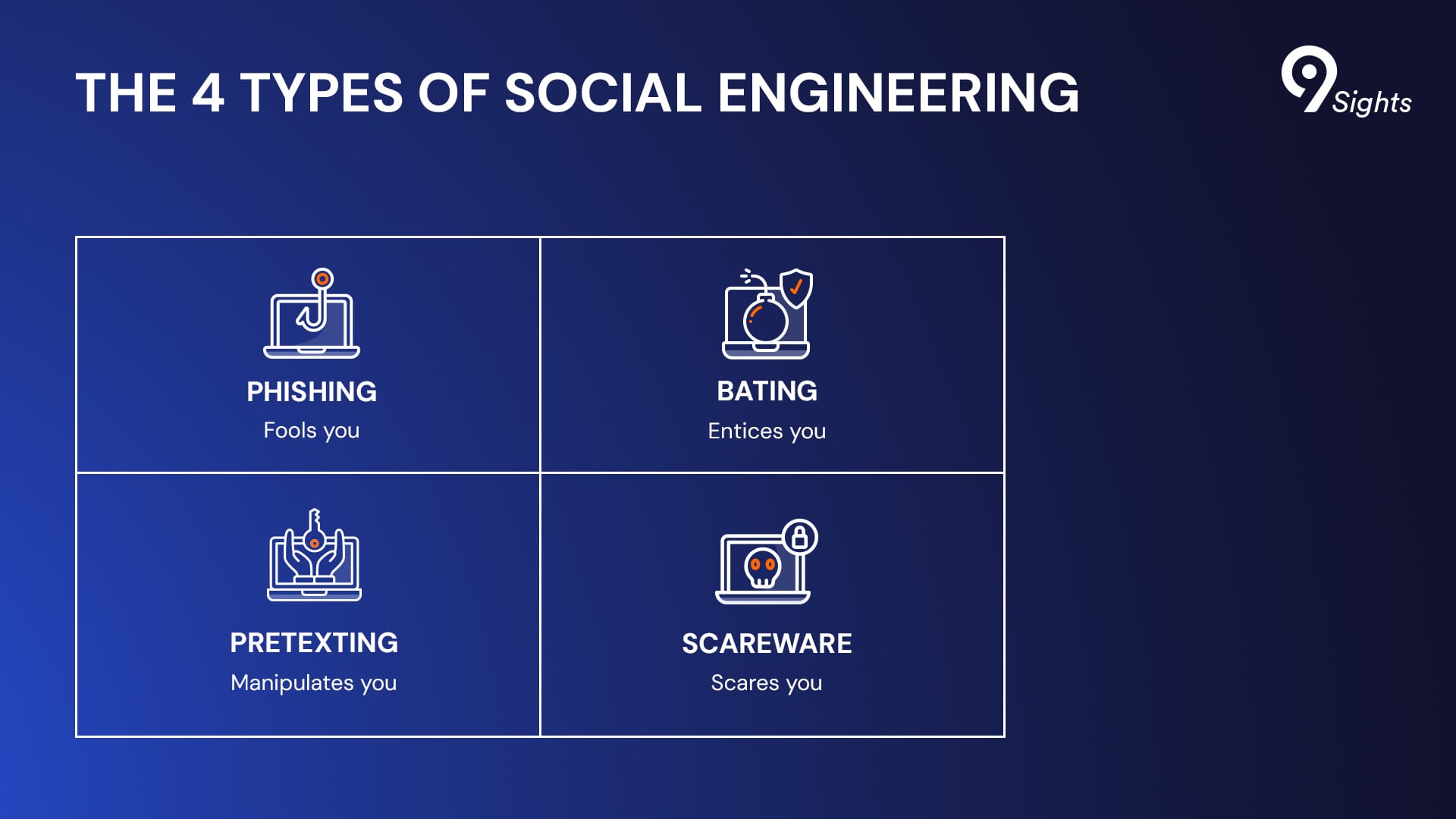
The primary entry point of cyber attacks is human error. Social engineering attacks come in various forms, such as:
Phishing: This is the most common form of human-focused attacks. Phishing convinces users to click malicious links, download infected files, or offer personal information. It has evolved into several specialized forms:
- Smishing: Phishing conducted via SMS
- Spear phishing: Targeted attacks against specific individuals or organizations
- Whaling: Attacks targeting high-level executives
Baiting: “Scammers make false promises to users in order to lure them into revealing personal information or installing malware on the system,” Cosmin explains. Common examples include promises of free products or exclusive content.
Pretexting: This approach is more sophisticated and involves creating convincing scenarios to gain trust. Attackers might present themselves as legitimate entities, such as investment companies, and they create a background story that convinces victims to provide sensitive information.
Scareware: This is one of the most manipulative approaches because it creates a sense of urgency around a fabricated problem. “The key difference is urgency,” says Cosmin. “A problem that requires immediate action – such as a virus infection – is presented alongside a supposed solution for it.”
Microsoft is the main target
Where human error is more damaging is where it can be combined with a weakness in the software. “Essentially, a vulnerability is either a design flaw, a misconfiguration, or any kind of bug that you have in the code,” outlines Levi9’s Python Tech Lead. These errors leave the gate open for attacks such as:
- SQL Injection
- Buffer overflow
- Cross-site scripting
- Man-in-the-middle attack
- Brute force
- Denial of service (DOS)
- Distributed denial of service (DDOS)
“… and many more that don’t have a name.” Many vulnerabilities don’t fall into a specific category.
Once the gate is open, hackers can steal data or push damaging software – also known as malware – to a target computer. The most popular types of malware are:
- Adware
- Spyware
- Ransomware
- Keylogger
- Bots
- Cryptojacking
- Virus
- Worm
- Rootkit
- Fileless Malware
The operating system a company uses can significantly impact its security profile. “Windows is by far the most targeted operating system, with 69 million new malware samples in 2022. Then we have Linux with 2 million and Android with 1 million.” Cosmin compares these with just 12,000 malware samples targeting macOS.
Hardware vulnerability is still a software issue
While phishing attempts and software vulnerabilities have a longer history, hardware has also become a potential gateway for an attack in recent years. “New hardware comes with code in the form of microcode or firmware,” Cosmin explains. As hackers start to realize that it can also be attacked, the hardware code is more difficult to fix than a software issue. “If it can be patched at all.”
The Spectre vulnerability, for example, “affects all modern CPUs, taking advantage of something called speculative execution.” This feature allows the processor to execute more branches of code before knowing the precise execution path. The flaw can be exploited to read protected data from anywhere in memory and then to search in the CPU cache for private data.
Understanding threat actors
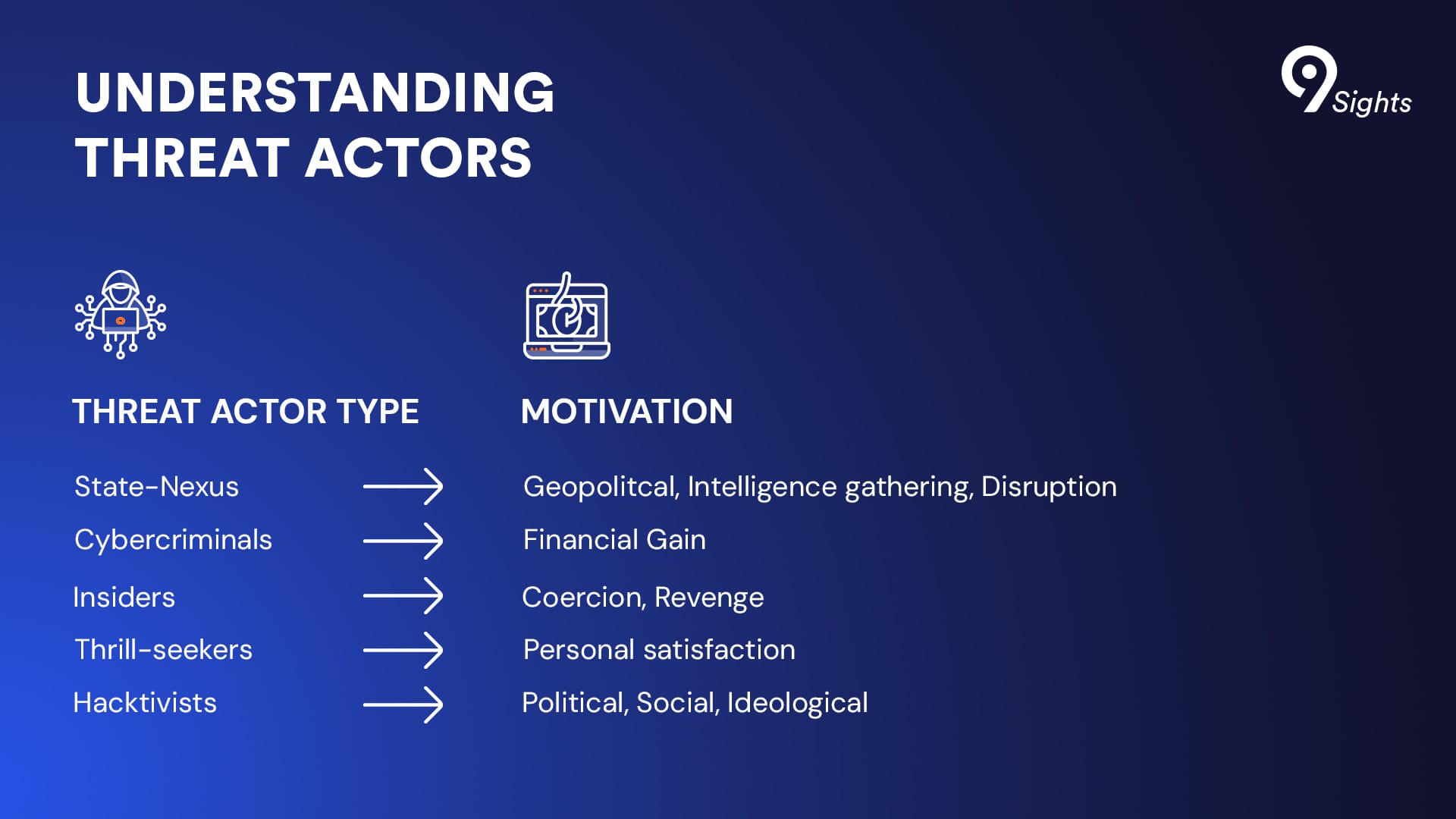
More than knowing your vulnerabilities, you must know your attackers. Peter Hudak explains that “different threat actors have different motivations” and outlines several key categories:
- Cybercriminals: Primarily motivated by profit, as seen in ransomware attacks
- Nation-States: Driven by geopolitical objectives
- Terrorist Groups: Pursuing ideological violence
- Thrill-seekers: Seeking personal satisfaction
- Insider Threats: Often motivated by discontent, revenge, financial gain, coercion
- Hacktivits: Ideological, political or social
Understanding these motivations helps security teams to watch out for certain attack methods. For instance, financially motivated cybercriminals prefer ransomware (26% of attacks), while ideologically driven actors often choose DDoS attacks. “Understanding the ‘why’ helps us understand better potential threats to our critical functions,” Peter notes. It also helps guide security efforts towards certain predictable types of attacks.

Red, blue and purple security teams
Modern cybersecurity has evolved beyond simple defense mechanisms. At ABN Amro Clearing, the approach uses two teams: The Operation & Intelligence Team(Blue Team) focuses on protection, detection, and response. The Infosec Testing Team(Red Team) conducts authorized Penetration testing and Red teaming. “When we work together, we call ourselves the Purple Team,” explains Peter.
Red Team exercises are more insightful because they’re not disclosed to the Blue Team. During these, members of Peter’s offensive security team will emulate the Techniques, Tactics and Procedures (TTP’s) of a Threat Actor and attempt to compromise critical functions. “Unlike standard Penetration tests, only limited group of people is disclosed about exercise execution,” Peter reveals. “This allows us to truly test not just our technical defenses but our entire organizational response.”
The battle of the machines
The introduction of artificial intelligence has brought the cyber battle to a new level. Antivirus software relies on machine learning to detect malicious files. “What happens more recently is that attackers start to use machine learning to make the files undetectable by the machine learning algorithms,” explains Cosmin. “So it’s machine learning versus machine learning.”
On top of that, AI can make social engineering attacks more sophisticated. AI can now generate highly convincing phishing emails, clone voices, or even create deepfake videos. Attacks can be both highly personalized and executed at scale.
To combat these evolving threats, organizations are turning to threat intelligence frameworks. Peter Hudak is pointing at the MITRE ATT&CK framework that provides a knowledge base of adversary tactics and techniques based on real-world observations. This framework helps security teams get an overview of potential attacks, map out potential attack vectors to their company, and develop appropriate countermeasures.
Upgrade for safety
For organizations that want to reduce the vulnerabilities, the first step is to have as few weak links as possible. This means training employees to never open files they don’t know the origin of. Cosmin also says that something as simple as frequent updates to software can help prevent most of the potential threats.
On top of that, companies should invest in gathering threat intelligence about potential threat actors that might be interested in their organization. Peter explains that having relevant threat intelligence helps organizations prioritize certain defenses, as they are not likely to be able to defend against everything.
While no system is bulletproof, awareness training, pro-active threat intelligence gathering, and keeping software updated can go a long way to preventing cyber attacks.
In this article: